1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
| 0000000000006000: ( ): jmp .+0 (0x00006002) ; eb00
0000000000006002: ( ): xor ecx, ecx ; 31c9
0000000000006004: ( ): cmp ecx, 0x00000081 ; 81f981000000
000000000000600a: ( ): jz .+226 (0x000060f2) ; 0f84e2000000
0000000000006010: ( ): xor esi, esi ; 31f6
0000000000006012: ( ): cmp esi, 0x00000009 ; 83fe09
0000000000006015: ( ): jz .+209 (0x000060ec) ; 0f84d1000000
000000000000601b: ( ): xor edx, edx ; 31d2
000000000000601d: ( ): mov eax, esi ; 89f0
000000000000601f: ( ): inc eax ; 40
0000000000006020: ( ): mov ebx, 0x00000009 ; bb09000000
0000000000006025: ( ): div eax, ebx ; f7f3
0000000000006027: ( ): mov edi, edx ; 89d7
0000000000006029: ( ): xor edx, edx ; 31d2
000000000000602b: ( ): mov eax, ecx ; 89c8
000000000000602d: ( ): mov ebx, 0x00000003 ; bb03000000
0000000000006032: ( ): div eax, ebx ; f7f3
0000000000006034: ( ): jz .+5 (0x0000603b) ; 7405
0000000000006036: ( ): jnz .+3 (0x0000603b) ; 7503
0000000000006038: ( ): ret 0x0099 ; c29900
000000000000603b: ( ): cmp edx, 0x00000000 ; 83fa00
000000000000603e: ( ): jz .+7 (0x00006047) ; 7407
0000000000006040: ( ): cmp edx, 0x00000001 ; 83fa01
0000000000006043: ( ): jz .+56 (0x0000607d) ; 7438
0000000000006045: ( ): jnz .+108 (0x000060b3) ; 756c
0000000000006047: ( ): shl esi, 0x02 ; c1e602
000000000000604a: ( ): mov eax, dword ptr ds:[esi] ; 3e8b06
000000000000604d: ( ): shl edi, 0x02 ; c1e702
0000000000006050: ( ): mov ebx, dword ptr ds:[edi] ; 3e8b1f
0000000000006053: ( ): mov edx, eax ; 89c2
0000000000006055: ( ): mov edi, ebx ; 89df
0000000000006057: ( ): or eax, ebx ; 09d8
0000000000006059: ( ): not edx ; f7d2
000000000000605b: ( ): not edi ; f7d7
000000000000605d: ( ): or edx, edi ; 09fa
000000000000605f: ( ): and eax, edx ; 21d0
0000000000006061: ( ): mov edx, eax ; 89c2
0000000000006063: ( ): mov ebx, 0x24114514 ; bb14451124
0000000000006068: ( ): mov edi, ebx ; 89df
000000000000606a: ( ): not eax ; f7d0
000000000000606c: ( ): not ebx ; f7d3
000000000000606e: ( ): and eax, ebx ; 21d8
0000000000006070: ( ): not eax ; f7d0
0000000000006072: ( ): and edx, edi ; 21fa
0000000000006074: ( ): not edx ; f7d2
0000000000006076: ( ): and eax, edx ; 21d0
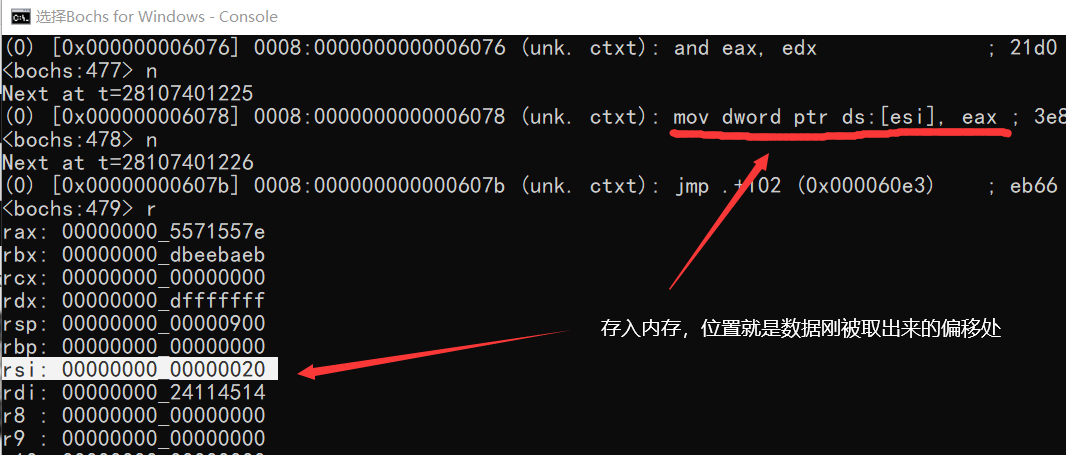
0000000000006078: ( ): mov dword ptr ds:[esi], eax ; 3e8906
000000000000607b: ( ): jmp .+102 (0x000060e3) ; eb66
000000000000607d: ( ): shl esi, 0x02 ; c1e602
0000000000006080: ( ): mov eax, dword ptr ds:[esi] ; 3e8b06
0000000000006083: ( ): shl edi, 0x02 ; c1e702
0000000000006086: ( ): mov ebx, dword ptr ds:[edi] ; 3e8b1f
0000000000006089: ( ): mov edx, eax ; 89c2
000000000000608b: ( ): mov edi, ebx ; 89df
000000000000608d: ( ): not eax ; f7d0
000000000000608f: ( ): not ebx ; f7d3
0000000000006091: ( ): and eax, ebx ; 21d8
0000000000006093: ( ): not eax ; f7d0
0000000000006095: ( ): and edx, edi ; 21fa
0000000000006097: ( ): not edx ; f7d2
0000000000006099: ( ): and eax, edx ; 21d0
000000000000609b: ( ): mov edx, eax ; 89c2
000000000000609d: ( ): mov ebx, 0x01919810 ; bb10989101
00000000000060a2: ( ): mov edi, ebx ; 89df
00000000000060a4: ( ): not ebx ; f7d3
00000000000060a6: ( ): and eax, ebx ; 21d8
00000000000060a8: ( ): not edx ; f7d2
00000000000060aa: ( ): and edx, edi ; 21fa
00000000000060ac: ( ): or eax, edx ; 09d0
00000000000060ae: ( ): mov dword ptr ds:[esi], eax ; 3e8906
00000000000060b1: ( ): jmp .+48 (0x000060e3) ; eb30
00000000000060b3: ( ): shl esi, 0x02 ; c1e602
00000000000060b6: ( ): mov eax, dword ptr ds:[esi] ; 3e8b06
00000000000060b9: ( ): shl edi, 0x02 ; c1e702
00000000000060bc: ( ): mov ebx, dword ptr ds:[edi] ; 3e8b1f
00000000000060bf: ( ): mov edx, eax ; 89c2
00000000000060c1: ( ): mov edi, ebx ; 89df
00000000000060c3: ( ): not ebx ; f7d3
00000000000060c5: ( ): and eax, ebx ; 21d8
00000000000060c7: ( ): not edx ; f7d2
00000000000060c9: ( ): and edx, edi ; 21fa
00000000000060cb: ( ): or eax, edx ; 09d0
00000000000060cd: ( ): mov edx, eax ; 89c2
00000000000060cf: ( ): mov ebx, 0x19260817 ; bb17082619
00000000000060d4: ( ): mov edi, ebx ; 89df
00000000000060d6: ( ): or eax, ebx ; 09d8
00000000000060d8: ( ): not edx ; f7d2
00000000000060da: ( ): not edi ; f7d7
00000000000060dc: ( ): or edx, edi ; 09fa
00000000000060de: ( ): and eax, edx ; 21d0
00000000000060e0: ( ): mov dword ptr ds:[esi], eax ; 3e8906
00000000000060e3: ( ): shr esi, 0x02 ; c1ee02
00000000000060e6: ( ): inc esi ; 46
00000000000060e7: ( ): jmp .-218 (0x00006012) ; e926ffffff
00000000000060ec: ( ): inc ecx ; 41
00000000000060ed: ( ): jmp .-238 (0x00006004) ; e912ffffff
00000000000060f2: ( ): xor ecx, ecx ; 31c9
00000000000060f4: ( ): xor edx, edx ; 31d2
00000000000060f6: ( ): cmp ecx, 0x00000012 ; 83f912
00000000000060f9: ( ): jz .+25 (0x00006114) ; 7419
00000000000060fb: ( ): shl ecx, 0x01 ; d1e1
00000000000060fd: ( ): mov ax, word ptr ds:[ecx-19092685] ; 3e668b8133abdcfe
0000000000006105: ( ): mov bx, word ptr ds:[ecx] ; 3e668b19
0000000000006109: ( ): cmp ax, bx ; 6639d8
000000000000610c: ( ): jz .+1 (0x0000610f) ; 7401
000000000000610e: ( ): inc edx ; 42
000000000000610f: ( ): shr ecx, 0x01 ; d1e9
0000000000006111: ( ): inc ecx ; 41
0000000000006112: ( ): jmp .-30 (0x000060f6) ; ebe2
0000000000006114: ( ): cmp edx, 0x00000000 ; 83fa00
0000000000006117: ( ): jnz .+98 (0x0000617b) ; 7562
0000000000006119: ( ): mov byte ptr gs:0x00000320, 0x41 ; 65c6052003000041
0000000000006121: ( ): mov byte ptr gs:0x00000321, 0x02 ; 65c6052103000002
0000000000006129: ( ): mov byte ptr gs:0x00000322, 0x63 ; 65c6052203000063
0000000000006131: ( ): mov byte ptr gs:0x00000323, 0x02 ; 65c6052303000002
0000000000006139: ( ): mov byte ptr gs:0x00000324, 0x63 ; 65c6052403000063
0000000000006141: ( ): mov byte ptr gs:0x00000325, 0x02 ; 65c6052503000002
0000000000006149: ( ): mov byte ptr gs:0x00000326, 0x65 ; 65c6052603000065
0000000000006151: ( ): mov byte ptr gs:0x00000327, 0x02 ; 65c6052703000002
0000000000006159: ( ): mov byte ptr gs:0x00000328, 0x73 ; 65c6052803000073
0000000000006161: ( ): mov byte ptr gs:0x00000329, 0x02 ; 65c605290300000
0000000000006169: ( ): mov byte ptr gs:0x0000032a, 0x73 ; 65c6052a03000073
0000000000006171: ( ): mov byte ptr gs:0x0000032b, 0x02 ; 65c6052b03000002
0000000000006179: ( ): jmp .+64 (0x000061bb) ; eb40
000000000000617b: ( ): mov byte ptr gs:0x00000320, 0x46 ; 65c6052003000046
0000000000006183: ( ): mov byte ptr gs:0x00000321, 0x04 ; 65c6052103000004
000000000000618b: ( ): mov byte ptr gs:0x00000322, 0x61 ; 65c6052203000061
0000000000006193: ( ): mov byte ptr gs:0x00000323, 0x04 ; 65c6052303000004
000000000000619b: ( ): mov byte ptr gs:0x00000324, 0x69 ; 65c6052403000069
00000000000061a3: ( ): mov byte ptr gs:0x00000325, 0x04 ; 65c6052503000004
00000000000061ab: ( ): mov byte ptr gs:0x00000326, 0x6c ; 65c605260300006c
00000000000061b3: ( ): mov byte ptr gs:0x00000327, 0x04 ; 65c6052703000004
00000000000061bb: ( ): jmp .-2 (0x000061bb) ; ebfe
|